
Threat Hunting: Envisioning SOC Operations with AI-Driven Hunts
Matt Rodgers
TLDR
The future of effective cybersecurity lies in revolutionizing threat hunting through AI and machine learning. Threat Hunting represents a paradigm shift in SOC operations—an AI-driven, continuously evolving system that works tirelessly in the background. Unlike static AI assistants, this agentic architecture allows for real-time updates and improvements, enabling SOC teams to stay ahead of emerging threats. By generating proactive hunt strategies and providing intelligent insights, it promises to dramatically reduce alert fatigue, enhance threat detection, and transform the SOC analyst’s role from reactive to proactive.
While this exact solution doesn’t exist yet, the concept points to a promising path for significantly improving SOC efficiency and effectiveness. As cyber threats continue to evolve, embracing such innovative approaches will be crucial for the next generation of cybersecurity defense.
Disclaimer: The opinions expressed in this post are my own and do not necessarily reflect the views of my employer or customers.
The SOC Struggle is Real
The last thing I heard before the security breach was, “Hey, the new threat detection system is up and running. We can all sleep easy tonight.” Spoiler alert: we couldn’t.
This incident became a stark reminder of the constant challenges in enterprise security, a field where I’ve been immersed since the early 2000s. I’ve seen the evolution of everything from firewalls to SIEM systems, and while we’ve come a long way, it’s clear we haven’t come far enough.
The Struggle with Traditional Threat Hunting
One of the core problems lies in the limitations of traditional threat hunting. By definition, threat hunting is based on a human-driven hypothesis—analysts form theories about potential threats and investigate them. While this approach can be effective, it’s inherently constrained by human capacity. We simply don’t have enough experienced analysts capable of crafting and testing hypotheses at the scale required to keep pace with the growing threat landscape. This shortage of skilled professionals leads to fewer hypotheses, fewer investigations, and an increased risk of missing critical events.

I recall one particularly grueling day in a major enterprise’s SOC. The team was plowing through tickets, confident in their progress. Unbeknownst to them, a critical breach was unfolding in real time, slipping through the cracks because no one had the bandwidth—or the right hypothesis—to catch it. By the time it was detected, the damage had already been done. This isn’t an isolated incident; it’s a symptom of the limitations of human-driven threat hunting.
The Opportunity with AI-Driven Threat Hunting
The opportunity here is clear: Threat hunting, powered by generative AI, offers a way to overcome the shortage of human hypotheses by automating the creation of potential attack scenarios. This allows SOC teams to expand their scope, investigate threats that may have been overlooked, and elevate the overall effectiveness of their operations.
Enter Threat Hunting: A Game-Changer for SOC Teams
Now, let’s talk about a concept that could revolutionize how SOC teams operate: threat hunting. Imagine an AI-driven system seamlessly integrated into your existing SOC tools, working alongside your threat hunting teams to provide a significant head start in identifying potential threats.
This concept can be further understood through the lens of agentic architectures, as detailed in a recent survey paper on AI agents Taxonomy of Agentic Architectures. These architectures highlight the role of autonomous agents that plan, reason, and execute complex tasks. In the context of threat hunting, a multi-agent system could be used to generate and execute proactive hunt strategies. For instance, one agent could act as a leader, orchestrating different agents that are responsible for specific functions, such as data correlation, log analysis, and attack path visualization.
AI-driven Multi-Agent Threat Hunting
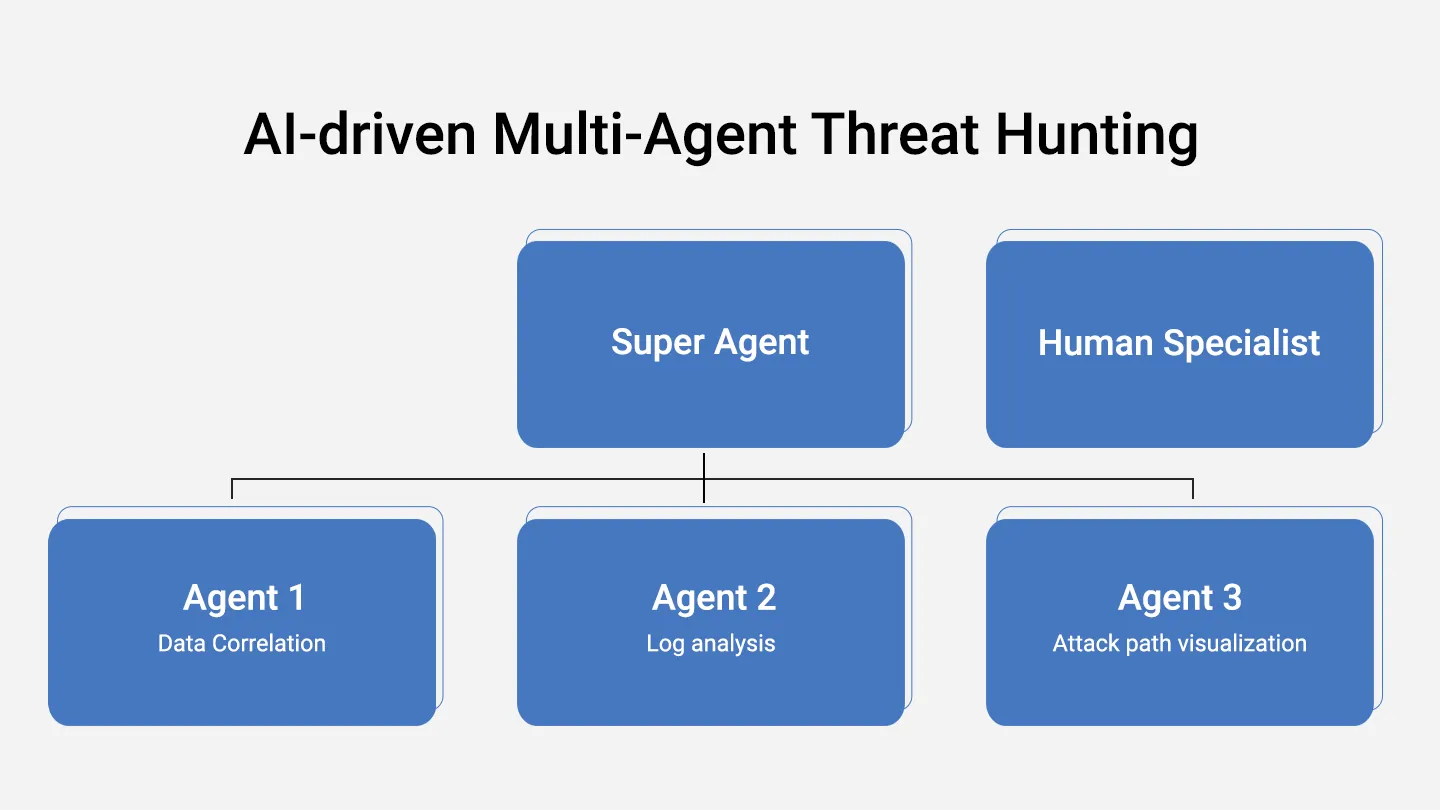
The paper outlines two primary types of architectures: single-agent and multi-agent systems. While single-agent systems excel in well-defined tasks, multi-agent systems thrive in environments requiring collaboration and multiple execution paths. In threat hunting, a multi-agent system could enhance the ability to investigate multiple scenarios simultaneously, leveraging different agent personas to conduct thorough and specialized investigations in parallel. This would make the SOC not just reactive but proactively scaling its capacity to hunt for threats.
The Opportunity with AI-Driven Threat Hunting
Here’s what a threat hunting system might look like in action:
- Holistic Data Integration: The threat hunting system would correlate data from various sources—asset information, identity data, and interactions across endpoints, networks, applications, and cloud environments. This integration would provide unmatched visibility across the entire security landscape.
- AI-Powered Scenario Generation: Leveraging this integrated data, the system would use generative AI to create potential threat scenarios. These scenarios could be developed through multi-agent reasoning, where different agents provide unique perspectives on a problem and collaborate to identify complex attack patterns.
- Proactive Hunt Strategies: Based on these scenarios, the system would automatically generate hunt strategies. In a multi-agent architecture, one agent might be responsible for planning, while others handle execution, tool use, or feedback collection.
- Interactive Visualization: The system would present its findings through an interactive interface. Analysts could explore complex relationships between entities, zoom in on suspicious patterns, and visualize potential attack paths that might otherwise go unnoticed.
- Continuous Learning: As hunt teams investigate these AI-generated leads, their findings would feed back into the system, refining its models and improving future hint generation.
Raising the Bar for Attackers
The aim of threat hunting is to make life significantly harder for attackers. By automating the hunt process and proactively identifying potential threats, we’re raising the bar. We’re closing those obvious vulnerabilities that attackers love to exploit, forcing them to work harder and potentially make mistakes that expose them.
According to Gartner’s 2024 predictions, “Generative AI will cause a spike in cybersecurity resources required to secure it, leading to a 15% increase in spend on application and data security through 2025.” The increasing sophistication of malicious actors demands machine-scale defenses, and threat hinting can be a crucial element in this next wave of cyber defense.
Beyond Alert Fatigue: Reinvigorating SOC Teams
Let’s face it—SOC work can be monotonous. Alert fatigue is real, and it’s a major factor in burnout and missed threats. Threat hunting has the potential to shake things up in a big way. Instead of slogging through endless alerts, your team could be:
- Investigating AI-generated scenarios that challenge their skills and creativity
- Uncovering complex, multi-stage attack attempts before they fully materialize
- Collaborating with AI to refine and improve threat detection strategies
The Road Ahead
While the concept of threat hunting is exciting, it’s important to note that we’re not quite there yet. This is a vision of what the future of cybersecurity could look like, but there are challenges to overcome:
- Data Integration: Bringing together data from disparate sources in a meaningful way is no small feat.
- AI Model Development: Creating AI models that can generate truly useful and creative scenarios will require significant R&D.
- User Experience: Designing an interface that presents complex AI-generated insights in an accessible way is crucial.
- Human-AI Collaboration: Developing workflows that effectively combine AI insights with human expertise will be key.
Gartner predicts that by 2028, “multiagent AI in threat detection and incident response will rise from 5% to 70% of AI implementations,” primarily to augment rather than replace staff. This shift will mark a new era in cybersecurity operations where AI plays an increasingly central role in enhancing the efficiency of SOC teams.
Recent advancements in AI for cybersecurity are paving the way for this vision. Leading companies are introducing AI assistants trained on vast security datasets, analyzing billions of events daily across web, email, endpoints, networks, and applications.

