Don’t Lose Sight of Business Continuity While Migrating to a New NaaS Service
Zaheer Aziz
IT supports the bread and butter of any business. A new technology introduction should minimize or prevent any business disruption. To migrate to a new NaaS (Network as a Service), serious consideration should be given in evaluating, planning and executing the migration. In this short article, my goal would be to share some standard migration best practices followed by an example of security migration to a new NaaS offer as in the case of SASE (Secure Access Services Edge) or SSE (Secure Services Edge). I have kept my approach vendor-agnostic so that it can be applied across the board.
Importance of Business Continuity
Business demands that any changes in the IT landscape should either improve the service or have no degradation. Any degradation in business continuity will most likely result in a roll back to the older service followed by serious questioning of the quality of the new solution. Imagine a manufacturing plant, which loses its production capability even for the shortest amount of time on the new solution will ask for a roll back.
Best Practices in Migrating to a New NaaS Service
There are generally two camps when it comes to adopting a new service. The first group takes a more cautious waterfall approach where the other one takes an agile methodology. An agile group wants to experiment with the technology after some evaluation where waterfall group likes to evaluate in depth before experimenting. Both approaches have merit and should be used as appropriate.
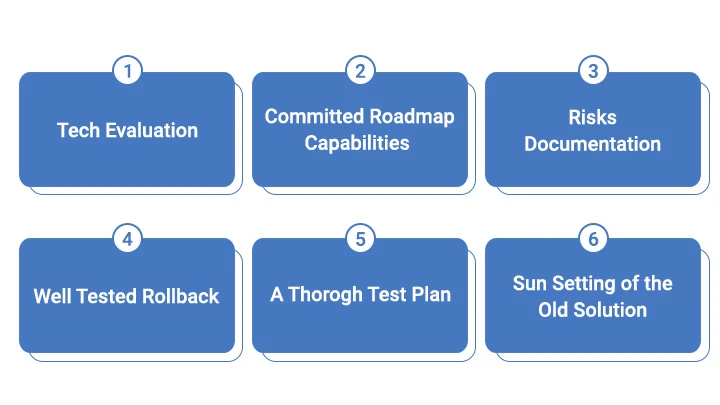

Post successful pilot comes a limited production rollout. The risks should be very carefully managed with all hands-on deck support and a clear rollback plan. A very thorough test plan should also be used to avoid any Monday morning blues.
Production rollout is ready when business has fully agreed and approved the new solution, a full communication plan along with schedules has been developed, and all support channels are ready. Timelines depends on the complexity and scale of the new solution. Once ready, teams generally move fast with batches of sites and users migrating at once. In many cases, migration automation helps tremendously. Careful observations should be made on the number of support tickets being generated due to the new solution. Similarly, constant improvements in migration windows should also be observed as teams are more comfortable and are using automation.
Then comes Sunsetting of the older solution which depends on many factors. Generally, it is contract dependent. If there is a contract term left on the solution, IT will consider keeping the old solution to go back to it in case disaster recovery when the new solution goes belly up. Eventually the older solution will be turned off with the return of equipment or reselling of the hardware.

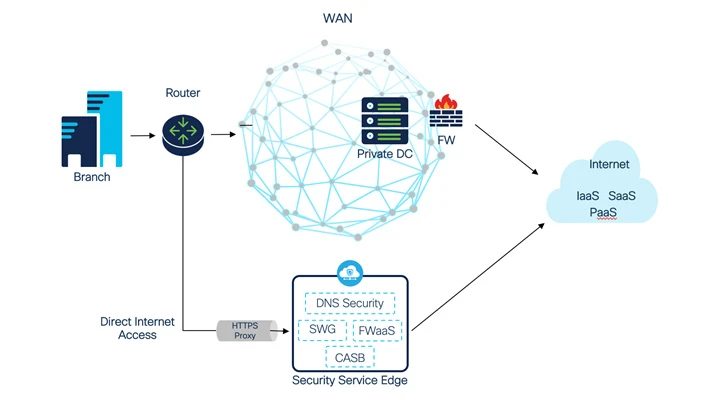
NaaS Example: Cloud Delivered Security Service
Traditional on-prem DMZ is slowly getting migrated or jointly served from a cloud-delivered security solution as in the case of SASE and SSE. However, for large IT shops, this isn’t that straightforward. For example, years and years of firewall rules, which BTW never gets cleaned up, must now be ported to the cloud solution.